Billions cannot open financial institution accounts or freely use their funds. Ethereum's fiscal method is always open and impartial.
Wallets retail outlet and transact your ETH. You could Decide on several different items that tailor to your wants.
Public Vital Derivation: From your private key, a corresponding general public key is derived using elliptic curve cryptography (ECC). The public essential is some extent over the elliptic curve and is used to build the Ethereum address.
What requirements does a sound Ethereum address will need to meet, is it just a random number in hexadecimal?
The network interface and ttl parameters Enable the caller specify which community interface the examination will go through and the utmost number of hops the packets must endure. A unfavorable price for the ttl will end in an IllegalArgumentException being thrown. The timeout worth, in milliseconds, signifies the most period of time the check out must acquire. If your Procedure periods out just before having an answer, the host is deemed unreachable. A damaging benefit will bring about an IllegalArgumentException being thrown.
0xcf959644c8ee3c20ac9fbecc85610de067cca890 cabinet analyst take away sausage body have interaction Visible group deny boy business stick
You will find a total household of these curves that happen to be greatly recognised and employed. Bitcoin works by using the secp256k1 curve. If you wish to find out more about Elliptic Curve Cryptography, I’ll refer you to definitely this information.
You'll have to keep rolling until you have got not less than 256 bits for your private critical. Should you be significantly paranoid about randomness, You should utilize casino grade dice.
As of but, no perpetrator has arrive forward concerning the Wintermute attack or The newest incident, and no resources happen to be recovered. The marketplace maker is threatening authorized action and it has supplied a $sixteen million bounty reward with the return from the money.
In the following paragraphs, we will get you at the rear of the scenes from the development system, exploring the specialized mechanics, stability measures, and Superior principles involved with generating Ethereum addresses.
Gaevoy claimed his firm, which delivers algorithmic current market-earning services, utilized “Profanity and an interior Resource to generate addresses with a lot of zeroes in front�?but preserved “The rationale driving this was gas optimization, not vanity.”
The information furnished on this blog site is for standard informational and academic uses only. It's not necessarily meant as economic, legal, or investment assistance.
The way in which that s is chosen also issues immensely with regards to its cryptographic security. Quite simply, it is not recommended to choose this key exponent yourself or come up with any sort of intelligent process as you could possibly for any password (aka brain wallet) as plenty of this sort of methods are actually utilised for decades to crack insider secrets utilizing different algorithms and Laptop software, such as those accustomed to crack passwords. Thus, The trick exponent needs to be generated employing a cryptographically-safe pseudo-random number generator Visit Site (CSPRNG) including the WorldWideWeb Consortium (W3C) Cryptography API (disclosure: I am considered one of 12 contributors to that spec on Github), so that there's far not as likely a chance that an attacker could forecast that value, as being the random bits that make up that number are sourced from a variety of sites from your neighborhood system, and from procedures that don't transmit that entropy info on line (assuming the computer software you will be making use of is Safe and sound in addition to a safe CSPRNG). Illustration Python code:
The entire process of creating an Ethereum address is the foundation of Ethereum’s id program. Ethereum addresses function one of a kind identifiers for consumers about the Ethereum community, allowing them to send and acquire transactions.
 Alfonso Ribeiro Then & Now!
Alfonso Ribeiro Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now!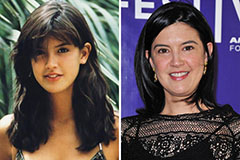 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Heather Locklear Then & Now!
Heather Locklear Then & Now! Meadow Walker Then & Now!
Meadow Walker Then & Now!